*JULY 6 UPDATE: MERCK Employees Federal Union Computer Systems still down.
On June 27 global headlines were buzzing about the second major global ransomware hacking attack in the past two months on large facilities and businesses around the world. The cyber attack originated in Ukraine but then quickly spread around the globe. Fortune reported the attack “…took down corporate networks at the Danish shipping company Maersk, American drugmaker Merck, Russian oil giant Rosneft, British ad agency WPP, and British law firm DLA Piper, among other places”
The mainstream corporate media headlines stayed with the cyber attack story for several days reporting on the progress companies were making and the hunt for the hack’s Ukrainian origins. The reporting and investigation on Merck went cold however. Few, if any, updates and no corporate media follow-up even while companies like Maersk were still grabbing front page headlines as the shipping giant struggled to shake off the cyber attack.
Within 24 hours after the attack, the analysis from tech publications like The Verge began to report that the ‘Petya’ virus was something worse than ransomware. Indeed, as the hours passed, many analysts, online coders and voices within cyberspace began to concur that Petya was not ransomware but was a ‘wiper’ virus specifically designed to lockdown computer systems and destroy data. On June 28, the day after the attack, Merck posted on Twitter the following:
“Our computer network was compromised on June 27 as part of a global cyber attack that affected other organizations worldwide. We immediately shut down our IT systems as a precautionary measure to help contain the problem and, where needed, moved to business continuity plans to ensure ongoing operations.”
On June 30, Merck’s last update in the complete absence of any mainstream media reporting, the company said it was working with “government authorities” who confirmed the ‘wiper’ malware contained “…a unique combination of characteristics that enabled it to effect company systems despite installation of recent software patches.” It can be assumed that a corporation would immediately implement internal measures for all employees to not speak to press or post on social media in a situation like Merck finds itself in.
At the time of this writing, all branches and computer systems of The Merck Employee Federal Credit Union, headquartered in New Jersey along with Merck’s US operations headquarters, are down or with limited access. The credit union, whose IT systems are shared with those of Merck, has instructed customers to use the ATM machines or mobile App photo capture feature for banking purposes. At the time of this writing, branches cannot process anything live.
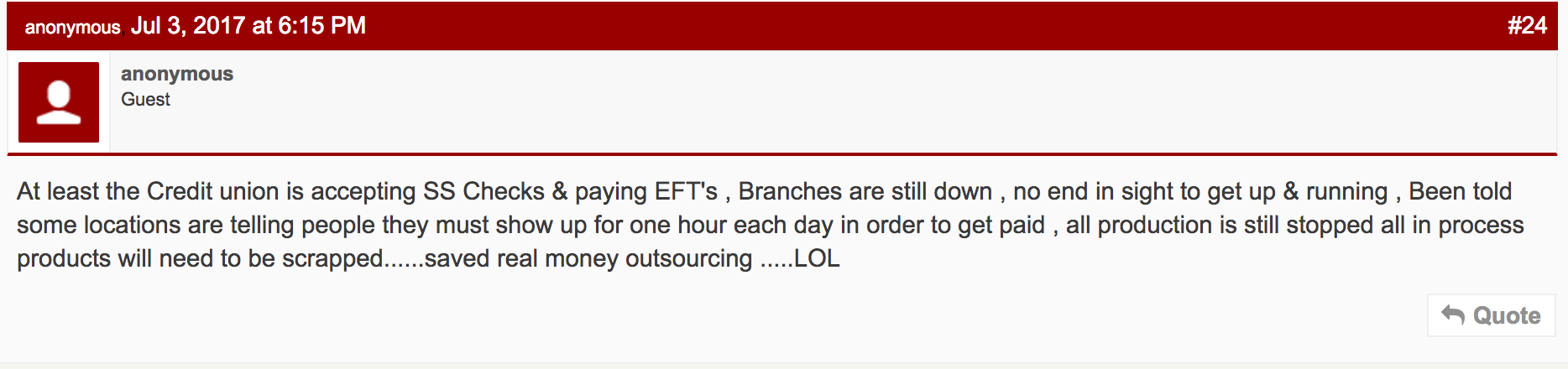
Cafepharma is a website for employees of pharmaceutical companies and job seekers to find employment and discuss pharma-related topics on its message board. The following posts were made under the thread titled “hackers” specifically discussing Merck’s Petya malware attack it is experiencing.
The mainstream corporate media headlines stayed with the cyber attack story for several days reporting on the progress companies were making and the hunt for the hack’s Ukrainian origins. The reporting and investigation on Merck went cold however. Few, if any, updates and no corporate media follow-up even while companies like Maersk were still grabbing front page headlines as the shipping giant struggled to shake off the cyber attack.
Within 24 hours after the attack, the analysis from tech publications like The Verge began to report that the ‘Petya’ virus was something worse than ransomware. Indeed, as the hours passed, many analysts, online coders and voices within cyberspace began to concur that Petya was not ransomware but was a ‘wiper’ virus specifically designed to lockdown computer systems and destroy data. On June 28, the day after the attack, Merck posted on Twitter the following:
“Our computer network was compromised on June 27 as part of a global cyber attack that affected other organizations worldwide. We immediately shut down our IT systems as a precautionary measure to help contain the problem and, where needed, moved to business continuity plans to ensure ongoing operations.”
On June 30, Merck’s last update in the complete absence of any mainstream media reporting, the company said it was working with “government authorities” who confirmed the ‘wiper’ malware contained “…a unique combination of characteristics that enabled it to effect company systems despite installation of recent software patches.” It can be assumed that a corporation would immediately implement internal measures for all employees to not speak to press or post on social media in a situation like Merck finds itself in.
At the time of this writing, all branches and computer systems of The Merck Employee Federal Credit Union, headquartered in New Jersey along with Merck’s US operations headquarters, are down or with limited access. The credit union, whose IT systems are shared with those of Merck, has instructed customers to use the ATM machines or mobile App photo capture feature for banking purposes. At the time of this writing, branches cannot process anything live.
Cafepharma is a website for employees of pharmaceutical companies and job seekers to find employment and discuss pharma-related topics on its message board. The following posts were made under the thread titled “hackers” specifically discussing Merck’s Petya malware attack it is experiencing.
The anonymous message board posts appears to paint a different picture within Merck's facility compared to the pharmaceutical company's official Twitter updates regarding its hack attack. No further information is publicly available regarding Merck’s current situation. If the company has been deeply compromised many questions about product production, job security of current employees, and global positioning would remain.
On July 5 it was announced that Petya malware authors have demanded $250,000 in their first public statement since the attack. As this story continues to develop, will mainstream media, who takes an estimated $5.4 billion from Big Pharma, report any information on the current condition of Merck’s internal situation?
On July 5 it was announced that Petya malware authors have demanded $250,000 in their first public statement since the attack. As this story continues to develop, will mainstream media, who takes an estimated $5.4 billion from Big Pharma, report any information on the current condition of Merck’s internal situation?








 RSS Feed
RSS Feed